
Table of Contents (Start)
- Topics
- Introducing SevOne
- Login
- Startup Wizard
- Dashboard
- Global Search - Advanced Search
- Report Manager
- Report Attachment Wizard
- Report Properties
- Report Interactions
- Instant Graphs
- TopN Reports
- Alerts
- Alert Archives
- Alert Summary
- Instant Status
- Status Map Manager
- Edit Maps
- View Maps
- FlowFalcon Reports
- NBAR Reports
- Logged Traps
- Unknown Traps
- Trap Event Editor
- Trap Destinations
- Trap Destination Associations
- Policy Browser
- Create and Edit Policies
- Webhook Definition Manager
- Threshold Browser
- Create and Edit Thresholds
- Probe Manager
- Discovery Manager
- Device Manager
- New Device
- Edit Device
- Object Manager
- High Frequency Poller
- Device Summary
- Device Mover
- Device Groups
- Object Groups
- Object Summary
- Object Rules
- VMware Browser
- AWS Plugin
- Azure Plugin (Public Preview)
- Calculation Plugin
- Database Manager
- Deferred Data Plugin
- DNS Plugin
- HTTP Plugin
- ICMP Plugin
- IP SLA Plugin
- JMX Plugin
- NAM
- NBAR Plugin
- Portshaker Plugin
- Process Plugin
- Proxy Ping Plugin
- SDWAN Plugin
- SNMP Plugin
- VMware Plugin
- Web Status Plugin
- WMI Plugin
- xStats Plugin
- Indicator Type Maps
- Device Types
- Object Types
- Object Subtype Manager
- Calculation Editor
- xStats Source Manager
- User Role Manager
- User Manager
- Session Manager
- Authentication Settings
- Preferences
- Cluster Manager
- Maintenance Windows
- Processes and Logs
- Metadata Schema
- Baseline Manager
- FlowFalcon View Editor
- Map Flow Objects
- FlowFalcon Views
- Flow Rules
- Flow Interface Manager
- MPLS Flow Mapping
- Network Segment Manager
- Flow Protocols and Services
- xStats Log Viewer
- SNMP Walk
- SNMP OID Browser
- MIB Manager
- Work Hours
- Administrative Messages
- Enable Flow Technologies
- Enable JMX
- Enable NBAR
- Enable SNMP
- Enable Web Status
- Enable WMI
- IP SLA
- SNMP
- SevOne Data Publisher
- Quality of Service
- Perl Regular Expressions
- Trap Revisions
- Integrate SevOne NMS With Other Applications
- Email Tips and Tricks
- SevOne NMS PHP Statistics
- SevOne NMS Usage Statistics
- Glossary and Concepts
- Map Flow Devices
- Trap v3 Receiver
- Guides
- Quick Start Guides
- AWS Quick Start Guide
- Azure Quick Start Guide (Public Preview)
- Data Miner Quick Start Guide
- Flow Quick Start Guide
- Group Aggregated Indicators Quick Start Guide
- IP SLA Quick Start Guide
- JMX Quick Start Guide
- Metadata Quick Start Guide
- RESTful API Quick Start Guide
- Self-monitoring Quick Start Guide
- SevOne NMS Admin Notifications Quick Start Guide
- SNMP Quick Start Guide
- Synthetic Indicator Types Quick Start Guide
- Topology Quick Start Guide
- VMware Quick Start Guide
- Web Status Quick Start Guide
- WMI Quick Start Guide
- xStats Quick Start Guide
- xStats Adapter - Accedian Vision EMS (TM) Quick Start Guide
- Deployment Guides
- Automated Build / Rebuild (Customer) Instructions
- Generate a Self-Signed Certificate or a Certificate Signing Request
- SevOne Best Practices Guide - Cluster, Peer, and HSA
- SevOne Data Platform Security Guide
- SevOne NMS Implementation Guide
- SevOne NMS Installation Guide - Virtual Appliance
- SevOne NMS Advanced Network Configuration Guide
- SevOne NMS Installation Guide
- SevOne NMS Port Number Requirements Guide
- SevOne NMS Upgrade Process Guide
- SevOne Physical Appliance Pre-Build BIOS and RAID Configuration Guide
- SevOne SAML Single Sign-On Setup Guide
- Cloud Platforms
- Other Guides
- Quick Start Guides
AWS Quick Start Guide
SevOne Documentation
All documentation is available from the IBM SevOne Support customer portal.
© Copyright International Business Machines Corporation 2024.
All right, title, and interest in and to the software and documentation are and shall remain the exclusive property of IBM and its respective licensors. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of IBM.
IN NO EVENT SHALL IBM, ITS SUPPLIERS, NOR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF IBM HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES, AND IBM DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE, AND NONINFRINGEMENT.
IBM, the IBM logo, and SevOne are trademarks or registered trademarks of International Business Machines Corporation, in the United States and/or other countries. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on ibm.com/trademark.
About
SevOne's AWS plugin allows you to collect devices, metadata, and metrics from the AWS environment right out-of-the-box. The plugin makes use of AWS CloudWatch metric streams for overtime data as well as for API calls for metadata enrichment. The AWS plugin allows you to monitor multiple different AWS accounts and regions.
Device Creation
SevOne NMS is configured, by default, to regularly call AWS APIs to retrieve information about the devices and then, automatically create devices for each AWS resource.
Required Infrastructure in AWS
To monitor an AWS account, the following necessary infrastructure in AWS must be configured.
-
Collector Role ARN
-
SQS Queue
-
Metric Stream
-
Firehose
-
S3 Bucket
This infrastructure is used to collect metrics for your AWS environment and make them available to SevOne NMS. Ensure that this is configured before continuing with the AWS plugin.
AWS Infrastructure can be set up in two ways: Terraform or AWS management console . Terraform is the recommended way that we will explain in details below. Please refer to section Appendix > Deploy AWS Resources using AWS Console to learn how to setup via AWS management console.
Deploy with Terraform
Terraform is the recommended way to configure the AWS resources. This allows for the quickest startup time while ensuring that resources are configured exactly as intended. To deploy and configure the required resources, a set of Terraform files can be found in /opt/SevOne-aws-collector/terraform directory. In order to run the Terraform files to create the resources, a role has been defined to maintain a least privileged posture. Let's refer to this role as Infrastructure Role.
Create a role for Terraform to use
A role can be created in two ways: Terraform or AWS management console . Terraform is the recommended way that we will explain in details below. Please refer to section Appendix > Create a Role via AWS Console for Terraform to use to learn how to create a role via AWS management console.
-
Using ssh , log in to SevOne NMS appliance as root .
$sshroot@<NMS appliance> -
Change directory to /opt/SevOne-aws-collector/terraform/envs/infrastructure_role.
-
Update the following values in terraform.tfvars.
Variable prefix must be,
-
between 1 and 20 characters
-
contain only lowercase letters, digits, or hyphens
-
start and end with letters or digits
account_id = <YOUR AWS ACCOUNT NUMBER>collector_user_arn = <USER ARN THAT WILL BE ABLE TO ASSUME THE ROLE>prefix = <PREFIX TO UNIQUELY IDENTIFY RESOURCES>Empty 'terraform.tfvars' file published with examples in comments## Your 12 digit AWS account number# account_id = 012345678901## AWS IAM User ARN that will be used to run the collector# collector_user_arn = "arn:aws:iam::012345678901:user/person@company.com"## Prefix to uniquely identify resources that are created in AWS## - Must be all lowercase due to S3 bucket naming restrictions# prefix = "sevone" -
-
Set the following environment variables.
exportAWS_ACCESS_KEY_ID="mykey"exportAWS_SECRET_ACCESS_KEY="mysecret"exportAWS_REGION="us-east-1" -
Apply the terraform files.
terraform initterraform planterraform applyPlease make note of output value, infrastructure_role_arn, as it will be required in section Run Terraform to deploy AWS resources below.
Run Terraform to deploy AWS resources
-
Using ssh , log in to SevOne NMS appliance as root .
$sshroot@<NMS appliance> -
Change directory to /opt/SevOne-aws-collector/terraform/envs/collector_infrastructure.
-
Update the following values in terraform.tfvars.
Variable prefix must be,
-
between 1 and 20 characters
-
contain only lowercase letters, digits, or hyphens
-
start and end with letters or digits
account_id = [YOUR AWS ACCOUNT NUMBER]collector_user_arn = [USER ARN THAT WILL BE ABLE TO ASSUME ROLE]infrastructure_role_arn = [ROLE ARN FOR INFRASTRUCTURE ROLE] (createdinlast step)regions = [ARRAY OF REGIONS TO CREATE RESOURCES IN]prefix = [PREFIX TO UNIQUELY IDENTIFY RESOURCES]Empty 'terraform.tfvars' file published with examples in comments## Your 12 digit AWS account number# account_id = 012345678901## AWS IAM User ARN that will be used to run the collector# collector_user_arn = "arn:aws:iam::012345678901:user/person@company.com"## AWS IAM Role ARN that will be used to install infrastructure## - This can be found in the output of applying the `infrastructure_role` Terraform config# infrastructure_role_arn = "arn:aws:iam::012345678901:role/sevone_infrastructure_role"## List of regions that you want to monitor# regions = ["us-east-1", "us-west-1"]## Prefix to uniquely identify resources that are created in AWS## - Must be all lowercase due to S3 bucket naming restrictions# prefix = "sevone"When adding more than one region to create the resources in, you can add it in terraform.tfvars file as,
Exampleregions = ["us-east-1","eu-central-1"] -
-
Apply the terraform files.
cdgenterraform initterraform planterraform applycd..terraform initterraform planterraform apply -
Details from the following output will be required to create a device in SevOne NMS .
-
account_id
-
collector_role_arn
-
sqs_queue
-
regions
-
Enable AWS Plugin
Execute the following steps to monitor an AWS account. This will automatically create devices and collect metrics for various AWS resources within selected regions for that account.
-
To access the Device Manager from the navigation bar, click the Devices menu and select Device Manager .
-
Either add a device with the AWS plugin or edit an existing device to enable the AWS plugin.
-
Click Add Device to display the New Device page.
-
Click the wrench icon under the Actions column to display the Edit Device page.
-
-
Click the plugin drop-down. By default, it is set to SNMP. Select AWS.
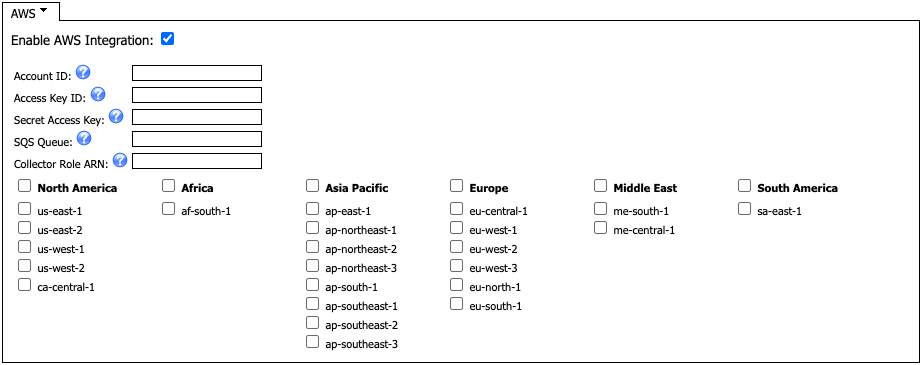
-
Select the Enable AWS Integration check box.
-
In the Account ID field, enter the ID of the account you want to monitor and collect data from.
-
In the Access Key ID field, enter the access key ID created for the collector user account. For additional details, please refer to https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html.
-
In the Secret Access Key field, enter the secret access key created for the collector user account. For additional details, please refer to https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html.
-
In the SQS Queue field, enter the SQS Queue name that the collector will listen to for metric stream events. For additional details, please refer to section Required Infrastructure in AWS.
-
In the Collector Role ARN field, enter the ARN of the IAM role that the collector will assume. For additional details, please refer to section Required Infrastructure in AWS.
-
Select / deselect the column headers or AWS region codes you want to collect data from.
-
Select or deselect a column header (for example, North America) to enable or disable collection for all regions underneath that header.
-
Select or deselect an AWS region code (for example, us-east-1) to enable or disable collection for that region.
-
-
Click Save As New to save the current changes as a New Device, or click Save to confirm the changes in the Edit Device page.
-
When the desired changes have been saved, click the Cancel button to return to the Device Manager page.
Once the device is created, collection of AWS resources starts on SevOne NMS.
Create TopN View in SevOne NMS to view AWS Resources
SevOne NMS contains a package with AWS-specific TopN views. To import, execute the following command.
$ SevOne-import --file /opt/SevOne-aws-collector/topn.spkThe import will fail unless the AWS collector has run successfully at least once.
OOTB Reports
The following out-of-the-box (OOTB) reports are available as part of SevOne Data Insight 6.5 and above.
-
AWS Direct Connect - report showing AWS Direct Connect inventory and network performance.
-
AWS EBS Volumes - report showing AWS EBS Volume performance.
-
AWS EC2 Report- report showing AWS EC2 inventory, CPU, disk, and network performance.
-
AWS NAT Gateway - report showing AWS NAT Gateway inventory, throughput and connection statistics.
-
AWS Network Load Balancers - report showing AWS Network Load Balancer statistics.
-
AWS S3 Report - report showing AWS S3 inventory and bucket statistics.
-
AWS Site to Site VPN - report showing AWS Site to Site VPN metrics.
-
AWS Transit Gateways - report showing AWS Transit Gateway inventory, network traffic, and drops.
Update AWS Infrastructure
SevOne NMS v6.6.0 supports more AWS resources to be monitored than v6.5.x. If you would like to monitor these newly supported AWS resources, please follow the steps below to update your AWS Infrastructure after an SevOne NMS upgrade from v6.5.x to v6.6.0.
Update a role for Terraform to use
-
Using ssh , log in to SevOne NMS appliance as root .
$sshroot@<NMS appliance> -
Change directory to /opt/SevOne-aws-collector/terraform/envs/infrastructure_role.
-
Apply the terraform files.
terraform initterraform planterraform applyPlease make note of output value, infrastructure_role_arn, as it will be required in section Run Terraform to deploy AWS resources below.
Run Terraform to deploy AWS resources
-
Using ssh , log in to SevOne NMS appliance as root .
$sshroot@<NMS appliance> -
Change directory to /opt/SevOne-aws-collector/terraform/envs/collector_infrastructure.
-
Apply the terraform files.
cdgenterraform initterraform planterraform applycd..terraform initterraform planterraform apply
Appendix
Deploy AWS Resources using AWS Console
AWS console allows you to create the AWS resource using the AWS console. While it is recommended to use Terraform, this is a viable option when that is not possible.
Create a Metric Stream
-
Navigate to CloudWatch > Metric Streams.
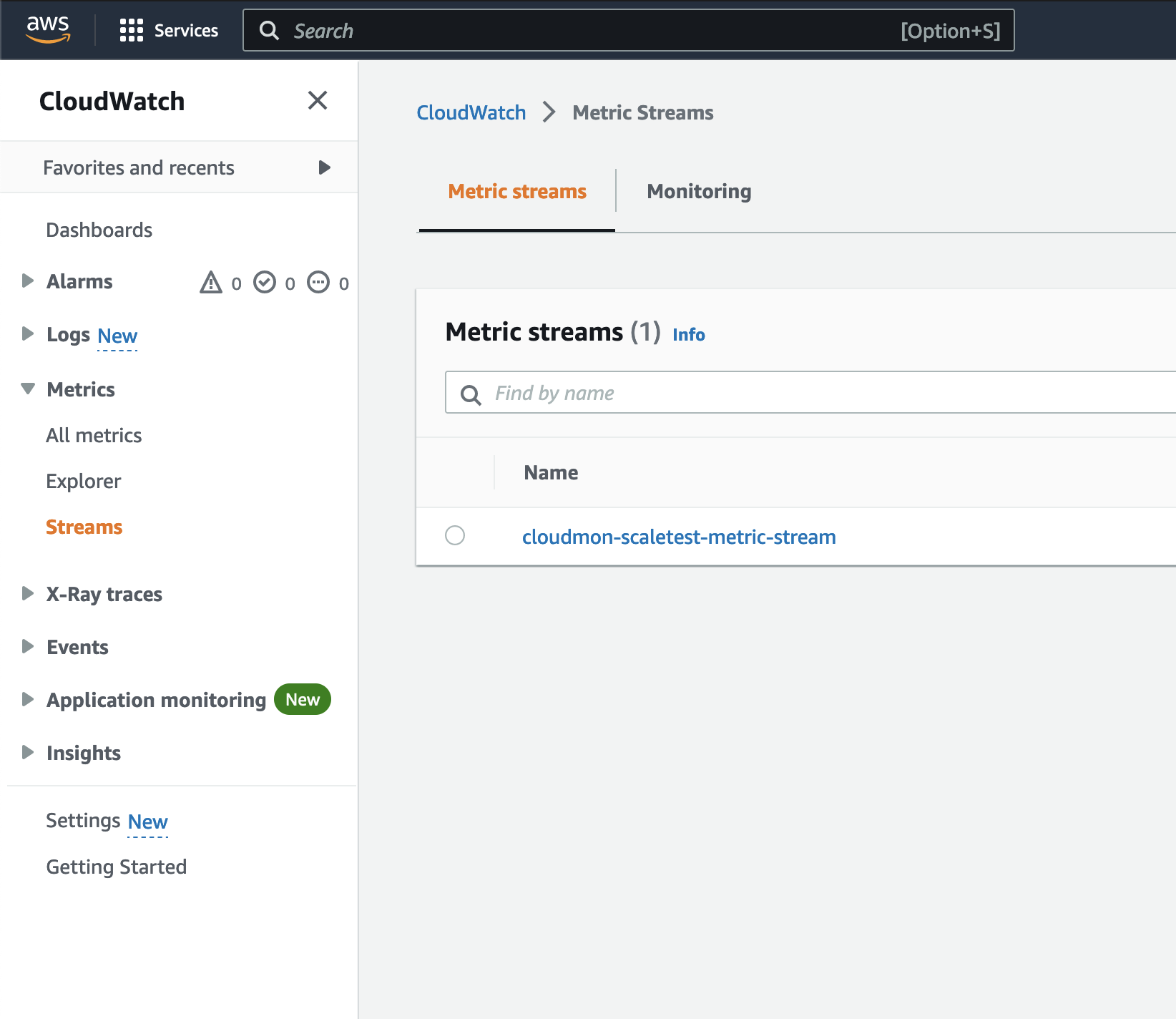
-
Click Create metric stream to launch the wizard.
-
Select the following namespaces.
-
AWS/EC2
-
AWS/S3
-
AWS/NATGateway
-
AWS/TransitGateway
-
AWS/DX
-
AWS/EBS
-
AWS/NetworkELB
-
AWS/VPN
-
-
Select Quick S3 setup check box.
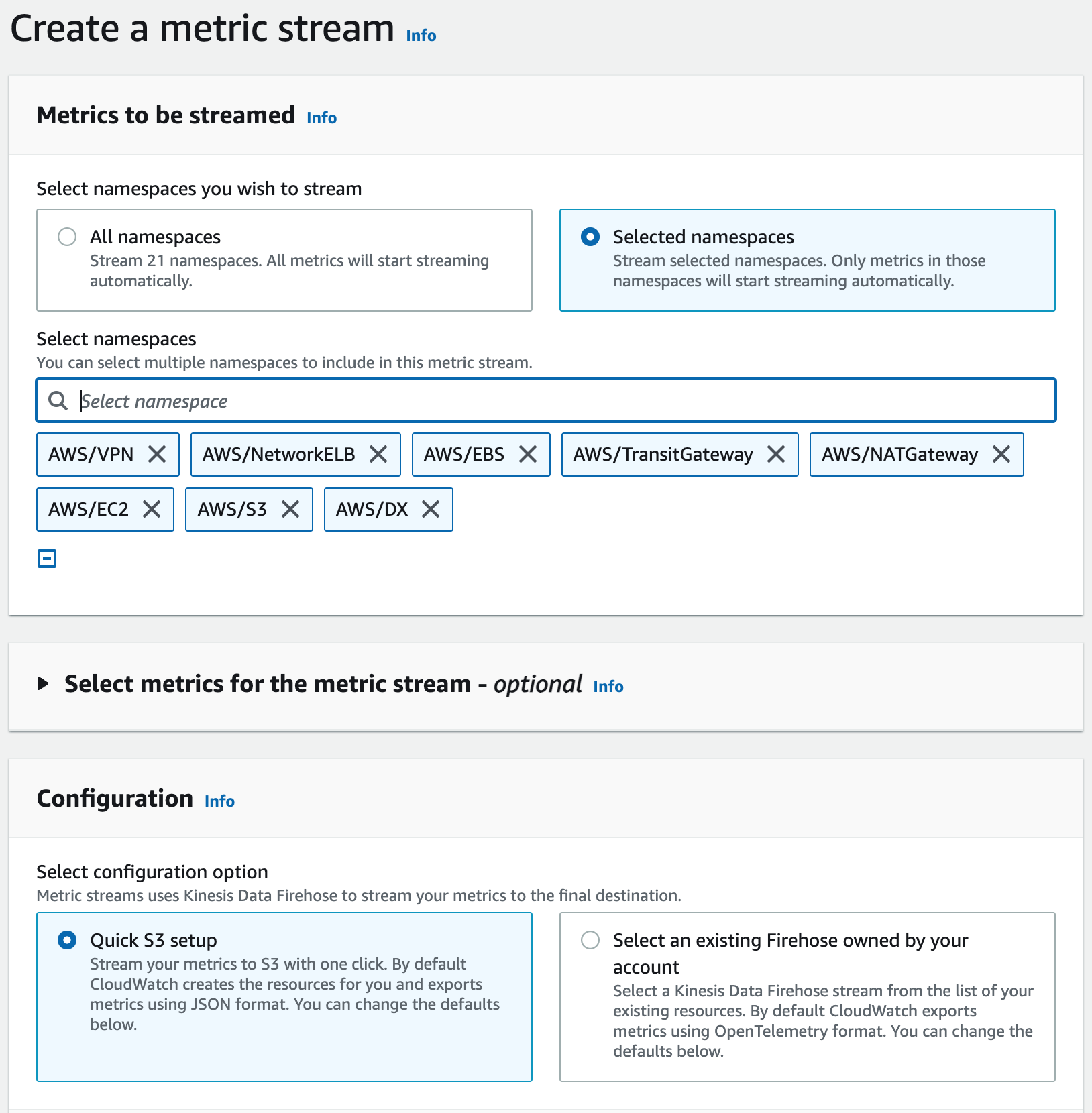
-
Rename the metric stream.
-
Click Create metric stream to complete the configuration.
Set up S3 Event Notifications
In https://docs.aws.amazon.com/AmazonS3/latest/userguide/ways-to-add-notification-config-to-bucket.html, follow steps 1. and 3a. to send all object create events to the SQS queue.
Create a Collector Role
Create a IAM role for the AWS plugin to use with the following policies.
Policy 'aws_collector_directconnect_policy'
{ "Version": "2012-10-17", "Statement": [ { "Sid": "", "Effect": "Allow", "Action": [ "directconnect:DescribeLocations", "directconnect:DescribeConnections" ], "Resource": "*" } ]}Policy 'sevone_collector_cloudwatch_policy'
{ "Version": "2012-10-17", "Statement": [ { "Sid": "", "Effect": "Allow", "Action": "cloudwatch:GetMetricData", "Resource": "*" } ]}Policy 'sevone_collector_ec2_policy'
{ "Version": "2012-10-17", "Statement": [ { "Sid": "", "Effect": "Allow", "Action": [ "ec2:DescribeInstances", "ec2:DescribeNatGateways", "ec2:DescribeTransitGateways", "ec2:DescribeVolumes", "ec2:DescribeVolumeStatus", "ec2:DescribeVpnConnections" ], "Resource": "*" } ]}Policy 'sevone_collector_elasticloadbalancing_policy'
{ "Version": "2012-10-17", "Statement": [ { "Sid": "", "Effect": "Allow", "Action": [ "elasticloadbalancing:DescribeLoadBalancers" ], "Resource": "*" } ]}Policy 'sevone_collector_s3_policy'
{ "Version": "2012-10-17", "Statement": [ { "Sid": "", "Effect": "Allow", "Action": [ "s3:ListAllMyBuckets", "s3:GetObject" ], "Resource": "*" } ]}Policy 'sevone_collector_sqs_policy'
{ "Version": "2012-10-17", "Statement": [ { "Sid": "", "Effect": "Allow", "Action": [ "sqs:ReceiveMessage", "sqs:GetQueueUrl", "sqs:DeleteMessage" ], "Resource": "*" } ]}Create a Role via AWS Console for Terraform to use
-
To create a new role,
-
from Services menu, select IAM.
-
select Roles from Access management menu.
-
select Create role.
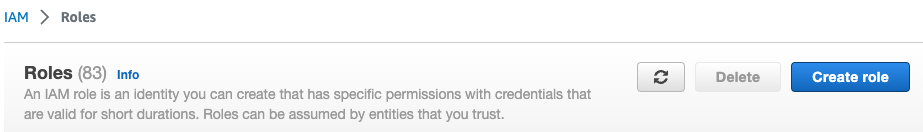
-
-
Allow Trust from This account.
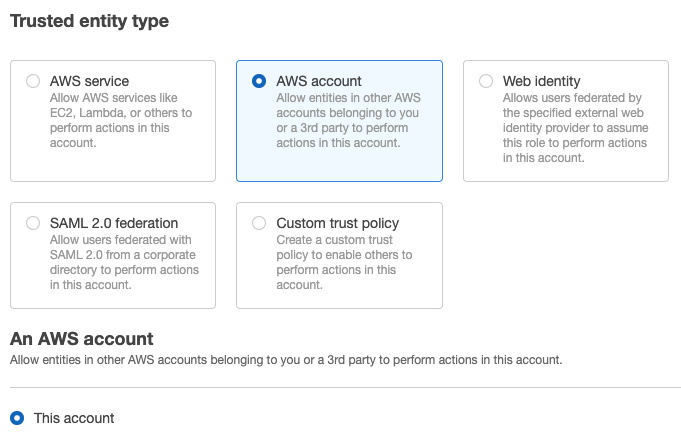
-
Add policies.
Example{"Version":"2012-10-17","Statement":[{"Action":["cloudwatch:TagResource","cloudwatch:ListTagsForResource"],"Effect":"Allow","Resource":"*","Sid":""},{"Action":["firehose:ListTagsForDeliveryStream","firehose:DescribeDeliveryStream","firehose:DeleteDeliveryStream","firehose:CreateDeliveryStream"],"Effect":"Allow","Resource":"*","Sid":""},{"Action":["iam:TagRole","iam:PutRolePolicy","iam:PassRole","iam:ListRolePolicies","iam:ListInstanceProfilesForRole","iam:ListAttachedRolePolicies","iam:GetRolePolicy","iam:GetRole","iam:DeleteRolePolicy","iam:DeleteRole","iam:CreateRole"],"Effect":"Allow","Resource":"*","Sid":""},{"Action":["cloudwatch:StopMetricStreams","cloudwatch:StartMetricStreams","cloudwatch:PutMetricStream","cloudwatch:ListMetricStreams","cloudwatch:GetMetricStream","cloudwatch:DeleteMetricStream"],"Effect":"Allow","Resource":"*","Sid":""},{"Action":["s3:PutObject","s3:PutLifecycleConfiguration","s3:PutBucketTagging","s3:PutBucketPublicAccessBlock","s3:PutBucketNotification","s3:PutBucketAcl","s3:ListBucket","s3:ListAllMyBuckets","s3:GetReplicationConfiguration","s3:GetLifecycleConfiguration","s3:GetEncryptionConfiguration","s3:GetBucketWebsite","s3:GetBucketVersioning","s3:GetBucketTagging","s3:GetBucketRequestPayment","s3:GetBucketPublicAccessBlock","s3:GetBucketPolicyStatus","s3:GetBucketPolicy","s3:GetBucketObjectLockConfiguration","s3:GetBucketNotification","s3:GetBucketLogging","s3:GetBucketLocation","s3:GetBucketCORS","s3:GetBucketAcl","s3:GetAccelerateConfiguration","s3:DeleteBucket","s3:CreateBucket"],"Effect":"Allow","Resource":"*","Sid":""},{"Action":["sqs:TagQueue","sqs:SetQueueAttributes","sqs:ListQueues","sqs:ListQueueTags","sqs:GetQueueUrl","sqs:GetQueueAttributes","sqs:DeleteQueue","sqs:CreateQueue"],"Effect":"Allow","Resource":"*","Sid":""}]}
-
Finish the Creation Wizard.
-
Allow Terraform to assume the newly created role.
-
Browse to IAM > Roles > Your newly created role > copy the ARN value.
-
Also, select Trust Relationships.
-
Ensure that the user for Terraform has permissions to assume the role.
Replace ${ACCOUNT_ID} and ${USERNAME} with real values.
Example{"Version":"2012-10-17","Statement": [{"Sid":"","Effect":"Allow","Principal": {"AWS": ["arn:aws:iam::${ACCOUNT_ID}:user/${USERNAME}","arn:aws:iam::${ACCOUNT_ID}:root"]},"Action":"sts:AssumeRole"}]}For additional details on creating AWS IAM roles, please refer to https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create.html.
-