
Table of Contents (Start)
- Topics
- Introducing SevOne
- Login
- Startup Wizard
- Dashboard
- Global Search - Advanced Search
- Report Manager
- Report Attachment Wizard
- Report Properties
- Report Interactions
- Instant Graphs
- TopN Reports
- Alerts
- Alert Archives
- Alert Summary
- Instant Status
- Status Map Manager
- Edit Maps
- View Maps
- FlowFalcon Reports
- NBAR Reports
- Logged Traps
- Unknown Traps
- Trap Event Editor
- Trap Destinations
- Trap Destination Associations
- Policy Browser
- Create and Edit Policies
- Webhook Definition Manager
- Threshold Browser
- Create and Edit Thresholds
- Probe Manager
- Discovery Manager
- Device Manager
- New Device
- Edit Device
- Object Manager
- High Frequency Poller
- Device Summary
- Device Mover
- Device Groups
- Object Groups
- Object Summary
- Object Rules
- VMware Browser
- AWS Plugin
- Azure Plugin (Public Preview)
- Calculation Plugin
- Database Manager
- Deferred Data Plugin
- DNS Plugin
- HTTP Plugin
- ICMP Plugin
- IP SLA Plugin
- JMX Plugin
- NAM
- NBAR Plugin
- Portshaker Plugin
- Process Plugin
- Proxy Ping Plugin
- SDWAN Plugin
- SNMP Plugin
- VMware Plugin
- Web Status Plugin
- WMI Plugin
- xStats Plugin
- Indicator Type Maps
- Device Types
- Object Types
- Object Subtype Manager
- Calculation Editor
- xStats Source Manager
- User Role Manager
- User Manager
- Session Manager
- Authentication Settings
- Preferences
- Cluster Manager
- Maintenance Windows
- Processes and Logs
- Metadata Schema
- Baseline Manager
- FlowFalcon View Editor
- Map Flow Objects
- FlowFalcon Views
- Flow Rules
- Flow Interface Manager
- MPLS Flow Mapping
- Network Segment Manager
- Flow Protocols and Services
- xStats Log Viewer
- SNMP Walk
- SNMP OID Browser
- MIB Manager
- Work Hours
- Administrative Messages
- Enable Flow Technologies
- Enable JMX
- Enable NBAR
- Enable SNMP
- Enable Web Status
- Enable WMI
- IP SLA
- SNMP
- SevOne Data Publisher
- Quality of Service
- Perl Regular Expressions
- Trap Revisions
- Integrate SevOne NMS With Other Applications
- Email Tips and Tricks
- SevOne NMS PHP Statistics
- SevOne NMS Usage Statistics
- Glossary and Concepts
- Map Flow Devices
- Trap v3 Receiver
- Guides
- Quick Start Guides
- AWS Quick Start Guide
- Azure Quick Start Guide (Public Preview)
- Data Miner Quick Start Guide
- Flow Quick Start Guide
- Group Aggregated Indicators Quick Start Guide
- IP SLA Quick Start Guide
- JMX Quick Start Guide
- Metadata Quick Start Guide
- RESTful API Quick Start Guide
- Self-monitoring Quick Start Guide
- SevOne NMS Admin Notifications Quick Start Guide
- SNMP Quick Start Guide
- Synthetic Indicator Types Quick Start Guide
- Topology Quick Start Guide
- VMware Quick Start Guide
- Web Status Quick Start Guide
- WMI Quick Start Guide
- xStats Quick Start Guide
- xStats Adapter - Accedian Vision EMS (TM) Quick Start Guide
- Deployment Guides
- Automated Build / Rebuild (Customer) Instructions
- Generate a Self-Signed Certificate or a Certificate Signing Request
- SevOne Best Practices Guide - Cluster, Peer, and HSA
- SevOne Data Platform Security Guide
- SevOne NMS Implementation Guide
- SevOne NMS Installation Guide - Virtual Appliance
- SevOne NMS Advanced Network Configuration Guide
- SevOne NMS Installation Guide
- SevOne NMS Port Number Requirements Guide
- SevOne NMS Upgrade Process Guide
- SevOne Physical Appliance Pre-Build BIOS and RAID Configuration Guide
- SevOne SAML Single Sign-On Setup Guide
- Cloud Platforms
- Other Guides
- Quick Start Guides
Authentication Settings
The Authentication Settings page enables you to configure SevOne NMS users to access the application via LDAP, RADIUS, and TACACS protocol authentication. The System Authentication tab enables you to upload security certificates.
To access the Authentication Settings page from the navigation bar, click the Administration menu, select Access Configuration, and then select Authentication Settings.
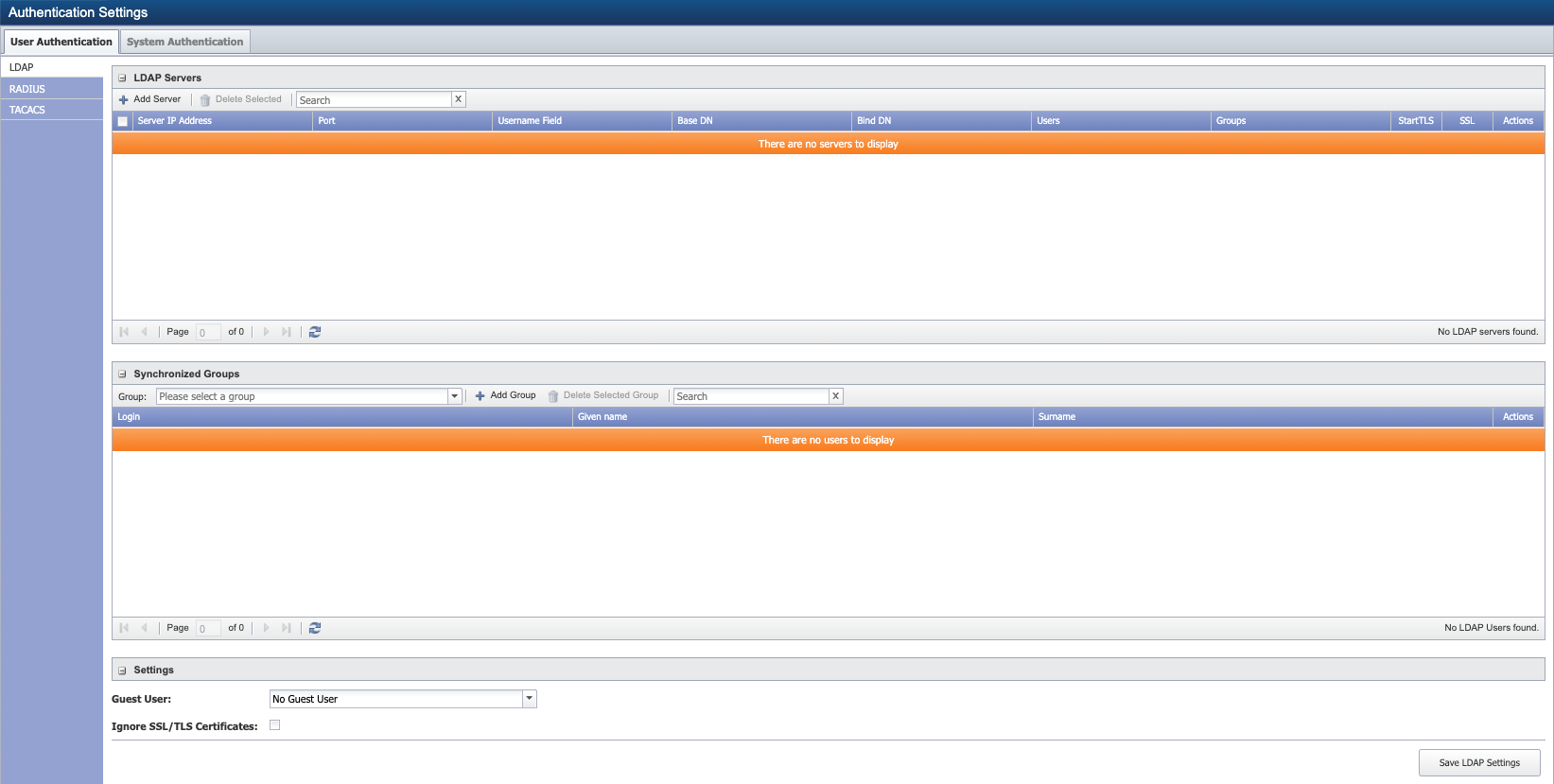
User Authentication
The User Authentication tab enables you to configure SevOne NMS to use LDAP, RADIUS, and TACACS protocol authentication.
-
Lightweight Directory Access Protocol (LDAP) - An application protocol to query and modify directory services that run over TCP/IP to enable maintenance of centralized user directories to which distributed applications authenticate.
-
Remote Authentication Dial In User Service (RADIUS) - A network protocol that provides centralized access, authorization and accounting management for people or computers to connect and use a network service.
-
Terminal Access Controller Access-Control System (TACACS) - A remote authentication protocol that communicates with an authentication server commonly used in UNIX networks.
LDAP
The LDAP subtab enables you to configure communication with the LDAP protocol authentication server.
LDAP refers to the Lightweight Directory Access Protocol. It is an industry standard application protocol for accessing and maintaining distributed directory information services over the IP network. Using LDAP, organizations can maintain centralized directories of users, groups, systems, networks, services, etc. Various distributed applications use LDAP to authenticate against those directories.
LDAP directories use a tree structure for storing information. This structure is known as a Directory Information Tree (DIT). The directory tree contains three main components:
-
Trunk
-
Branches
-
Leaves
The trunk is the directory root. It will most likely be named after a domain. For example, if your domain is example.com, the root of your directory would be named dc=example, dc=com. The branches of the trunk are organizational units. If your organization has multiple sites, you might have an organizational unit, or ‘ou’, for each site. For example, you could have one ou for California, another one for Texas, and another for Pennsylvania and as many ou’s as you wish.
Just as an individual branch can have its own branches, an ou can have, or contain, its own ou’s. The ou’s mentioned above might each contain three subordinate ou’s: Users ou, a Groups ou, and a Machines ou. These ou’s can also contain ou’s, but they do not have to. The Users ou, for instance, might just contain the users for that location. The actual user entries would be considered leaves because they cannot contain any subordinate entries.
A few benefits of the tree structure are:
-
Increased ease of administration and maintenance
-
Flexible application of security policies and access controls
-
Scalability
-
Simplified resource sharing
Common systems that provide implementations of LDAP include Microsoft's ActiveDirectory, the open source OpenLDAP project, and the Oracle Internet Directory product line.
SevOne NMS supports LDAP authentication for individual users and LDAP group synchronization for Active Directory and OpenSSL. Group synchronization occurs once per hour. A user group in LDAP creates a user role in SevOne NMS, however, manually adding a user to that role may result in automatically removing the added user from that role and/or deleting it from SevOne NMS.
Any LDAP authenticated user who has the Must Change Password at Next Logon (or similar) setting on the LDAP server and has NOT changed said password will NOT be able to log on to SevOne NMS. Either disable this setting for the user on the LDAP server or ensure that LDAP users change their passwords elsewhere before attempting to log on SevOne NMS.
When LDAP Group Synchronization is enabled, SevOne NMS attempts to synch LDAP users from any configured groups into the SevOne NMS user repository on an hourly basis. Relevant properties are populated per the following:
-
givenname -> Given Name
-
sn -> Surname
-
mail -> Email
Perform the following steps to manage LDAP authentication.
LDAP Servers
SevOne NMS maintains consistency between the remote LDAP server and the synced local users who have only an LDAP role. This means that when such a user is removed from the remote LDAP server, SevOne NMS also removes the corresponding local user.
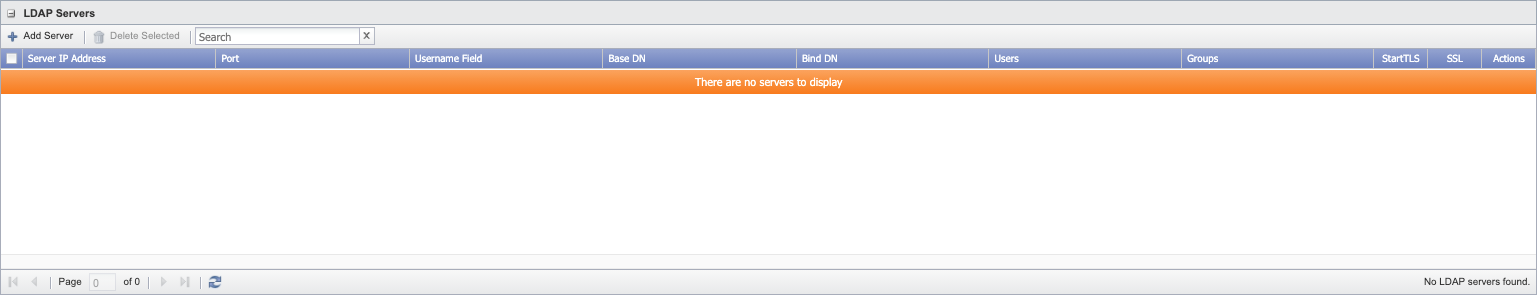
-
In the LDAP Servers section, click Add Server above the server list or click
 to display the Add/Edit LDAP Server pop-up.
to display the Add/Edit LDAP Server pop-up. 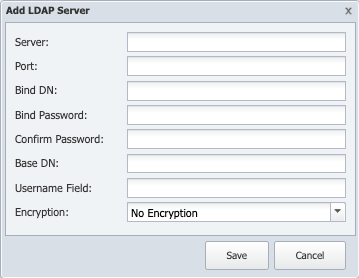
-
In the Server field, enter the host name or IP address of the LDAP server.
-
In the Port field, enter the network port of the LDAP server. The default LDAP port is 389. The default LDAPS port is 636 which has been deprecated.
-
In the Bind DN field, enter the name of the user SevOne NMS is to use to authenticate to the directory. This is the username that is authorized to perform searches within the context of the Base DN in the previous step, which means that the bind DN's authorizations also allow SevOne NMS to search the directory tree.
Example: Bind DNCN=SevOne Bind,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=net
-
In the Bind Password field, enter the password for the user name you enter in the previous step. This is not required in LDAP version 3 (LDAPv3).
-
In the Confirm Password field, reenter the bind password.
-
In the Base DN field, enter the base distinguished name (DN) on which to perform the LDAP queries. For standard configuration, the top level of the LDAP directory tree is the base, referred to as the base DN from which a search starts.
Example: Base DNDC=itl-pub-ad01,DC=sevitlab,DC=net
-
In the Username Field, enter the Distinguished Name that uniquely identifies and describes an entry in a directory (LDAP) server. For example, sAMAccountName is suggested to be used as the Distinguished Name.
-
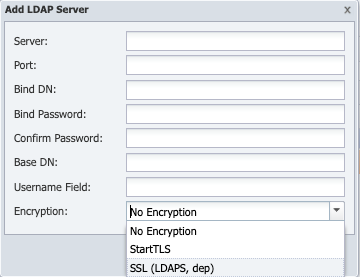
Click the Encryption drop-down.
-
Select No Encryption to not use encryption.
-
Select StartTLS to use StartTLS. StartTLS secures the LDAP credentials and data. StartTLS is sometimes referred to as the TLS upgrade operation because it upgrades a normal LDAP connection to a connection that is protected by TLS/SSL.
-
Select SSL (LDAPS, dep) to use Secure Socket Layers (SSL). SSL secures LDAP data. A method to secure LDAP communication is to use an SSL tunnel. This is denoted in LDAP URLs by using the URL scheme "ldaps". The use of LDAP over SSL was common in LDAPv2. This usage has been deprecated along with LDAPv2.
Example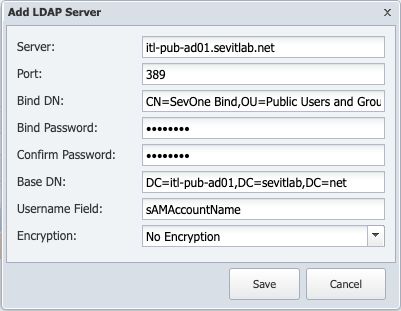
-
-
Click Save.
-
-
Repeat to add additional servers.
-
In the server list, the StartTLS column and the SSL column enable you to change the related settings.
-
Click
 in the Actions column to test the connection to the LDAP server.
in the Actions column to test the connection to the LDAP server.
Standard LDAP Configuration
This section is being provided to demonstrate the use of the LDAP search command with the default LDAP database settings.
The LDAP database settings are available from the Command Line Interface and are not exposed from SevOne NMS Graphical User Interface.
By default, SevOne is delivered with the following in the LDAP's settings table.
-
Using ssh , log in to SevOne NMS appliance as root .
$sshroot@<NMS appliance> -
Enter the following command to see what the database looks like for a standard NMS LDAP setup.
$ mysqldata -e"select * from settings where setting like '%ldap%';"+-------------------------+-------------------------------------------------------------+| setting | value |+-------------------------+-------------------------------------------------------------+| ldap_never_cert | 0 || ldap_group_criteria | (|(groupType=*)(objectClass=group)(objectClass=posixGroup)) || ldap_possible_members | member,memberuid || ldap_member_criteria | user,posixAccount || ldap_subgroup_criteria | group,posixGroup || ldap_member_criteria_ad | (|(objectClass=user)(objectCategory=person)) |+-------------------------+-------------------------------------------------------------+Please make a note of the following values:
-
(|(groupType=*)(objectClass=group)(objectClass=posixGroup)) returned for setting ldap_group_criteria.
-
(|(objectClass=user)(objectCategory=person)) returned for setting ldap_member_criteria_ad.
If any changes are made to these database entries, the changes can be verified using the following LDAP search commands with your specified changes.
-
-
LDAP search can be performed on Groups or Users.
LDAP-search for GROUPS$ ldapsearch -H ldap:<enter LDAP server:Port Number> \-b"<enter Base DN>"\-D"<enter Bind DN>"\-w'<enter your password for LDAP search>'"<enter ldap_group_criteria>"-Lwhere ldap_group_criteria is returned from mysqldata command for the standard NMS LDAP setup above.
Example: for group 'Group A-M',$ ldapsearch -H ldap://itl-pub-ad01.sevitlab.net:389 \-b"DC=itl-pub-ad01,DC=sevitlab,DC=net"\-D"CN=SevOne Bind,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=net"\-w'sevoneldap'"(|(groupType=*)(objectClass=group)(objectClass=posixGroup))"-L.........# Group A-M, Public Users and Groups 01, itl-pub-ad01.sevitlab.netdn: CN=Group A-M,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=netobjectClass:topobjectClass: groupcn: Group A-Mmember: CN=Michelle Doe,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=net......member: CN=Edward Doe,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=net......member: CN=Brad Doe,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=net......member: CN=Aaron Doe,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=netdistinguishedName: CN=Group A-M,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=netinstanceType: 4whenCreated: 20150630232826.0ZwhenChanged: 20150701135404.0ZuSNCreated: 12740uSNChanged: 20927name: Group A-MobjectGUID:: Ufjdj9pv6Uul+UyW1eG+UA==objectSid:: AQUAAAAAAAUVAAAAh4KcDHX6ddRUL+l8UAQAAA==sAMAccountName: Group A-MsAMAccountType: 268435456groupType: -2147483646objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=itl-pub-ad01,DC=sevitlab,DC=netdSCorePropagationData: 16010101000000.0Z.........where, Michelle Doe, Edward Doe, Brad Doe, and Aaron Doe are the users in Group A-M.
For standard configuration, sAMAccountName is used as a Distinguished Name that uniquely identifies and describes an entry in a directory (LDAP) server.
In the example above, sAMAccountName for Group A-M is Group A-M.
LDAP-search for USERS$ ldapsearch -H ldap:<enter LDAP server:Port Number> \-b"<enter Base DN>"\-D"<enter Bind DN>"\-w'<enter your password for LDAP search>'"<enter ldap_group_criteria>"-Lwhere ldap_group_criteria is returned from mysqldata command for the standard NMS LDAP setup above.
Example: for user 'Edward Doe',$ ldapsearch -H ldap://itl-pub-ad01.sevitlab.net:389 \-b"DC=itl-pub-ad01,DC=sevitlab,DC=net"\-D"CN=SevOne Bind,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=net"-w'sevoneldap'"(|(objectClass=user)(objectCategory=person))"-L.........# Edward Doe, Public Users and Groups 01, itl-pub-ad01.sevitlab.netdn: CN=Edward Doe,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=netobjectClass:topobjectClass: personobjectClass: organizationalPersonobjectClass: usercn: Edward Doesn: Doec: ENgivenName: Edwardinitials: EDdistinguishedName: CN=Edward Doe,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=netinstanceType: 4whenCreated: 20150630234233.0ZwhenChanged: 20150630234233.0ZdisplayName: Doe,ED EdwarduSNCreated: 20624memberOf: CN=Group A-M,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=netuSNChanged: 20630name: Edward DoeobjectGUID:: jFD3wo4Ruk2MPY3/inMOHg==userAccountControl: 66048badPwdCount: 0codePage: 0countryCode: 0badPasswordTime: 0lastLogoff: 0lastLogon: 0pwdLastSet: 130801813536586777primaryGroupID: 513objectSid:: AQUAAAAAAAUVAAAAh4KcDHX6ddRUL+l8YgQAAA==accountExpires: 9223372036854775807logonCount: 0sAMAccountName: msad-edwardsAMAccountType: 805306368userPrincipalName: msad-edward@itl-pub-ad01.sevitlab.netobjectCategory: CN=Person,CN=Schema,CN=Configuration,DC=itl-pub-ad01,DC=sevitlab,DC=netdSCorePropagationData: 20150630234233.0ZdSCorePropagationData: 16010101000000.0Zmanager: CN=Manager Dude,OU=Public Users and Groups 01,DC=itl-pub-ad01,DC=sevitlab,DC=net.........For standard configuration, sAMAccountName is used as a Distinguished Name that uniquely identifies and describes an entry in a directory (LDAP) server.
In the example above, sAMAccountName for user Edward Doe is msad-edward which is the username (login name).
Synchronized Groups
From SevOne NMS > Administration > Access Configuration > Authentication Settings > under tab User Authentication, choose LDAP and add an LDAP Server as described in section LDAP Servers above. In the Synchronized Groups section, click the Group drop-down and select the server group to which to associate the server you select.
If no group is available, add a group; please refer to section Add Group below. Once you have added a group, you will see itl-pub-ad01.sevitlab.net Group A-M, for example, from the Group drop-down list.
Select group itl-pub-ad01.sevitlab.net Group A-M and it will list all the users in Group A-M.
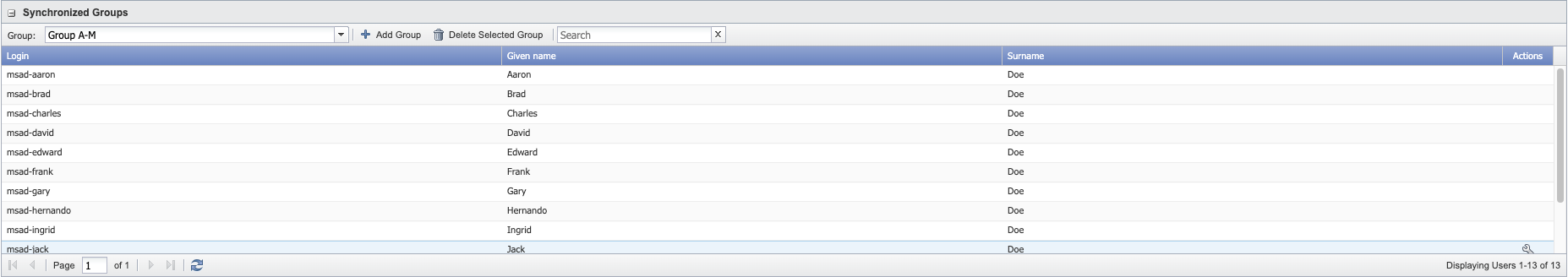
LDAP groups are the equivalent of SevOne NMS user roles.
Since group itl-pub-ad01.sevitlab.net Group A-M is selected from Group drop-down list, all users assigned to Group A-M are added to Administration > Access Configuration > User Manager. For example, msad-michelle, msad-edward, msad-brad, msad-aaron, etc.
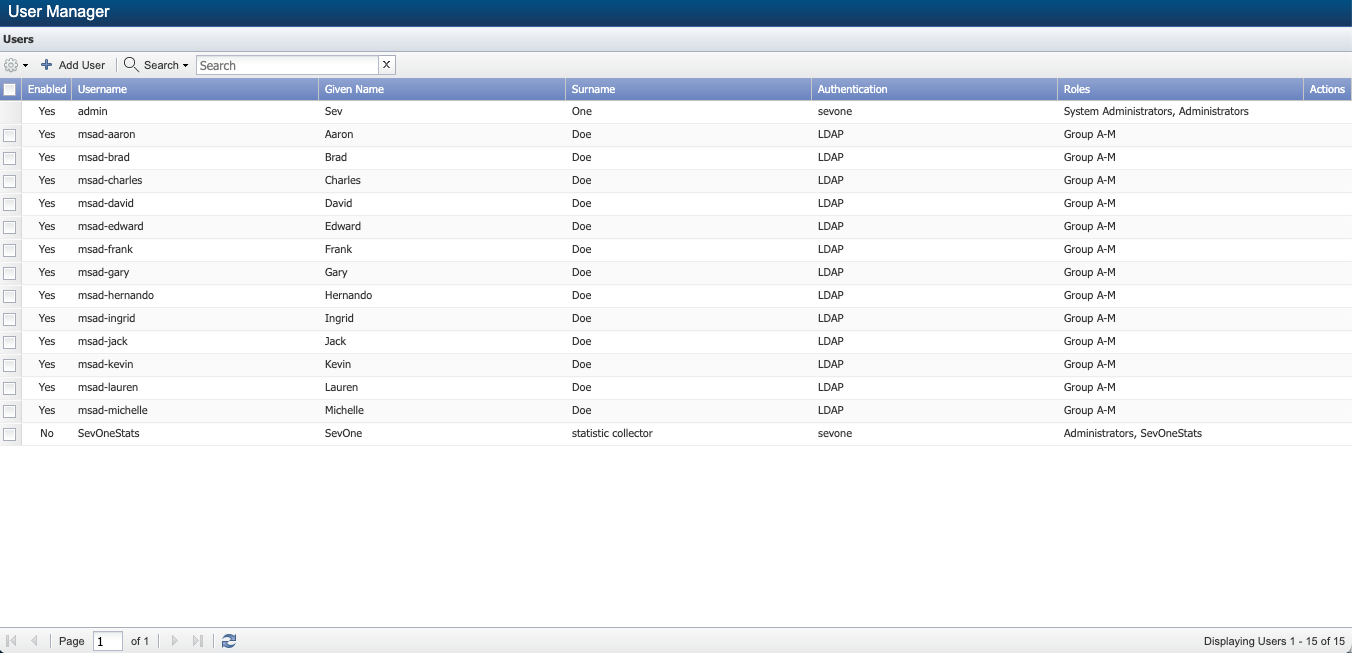
From SevOne NMS > Administration > Access Configuration > User Role Manager > under Roles in left navigation bar, you will now see LDAP and it contains group Group A-M under All Roles > System Administrators > Administrators. Click LDAP and in the right pane, tab Permissions > you can set the desired permissions. The permissions set will apply to all group(s) available under LDAP.
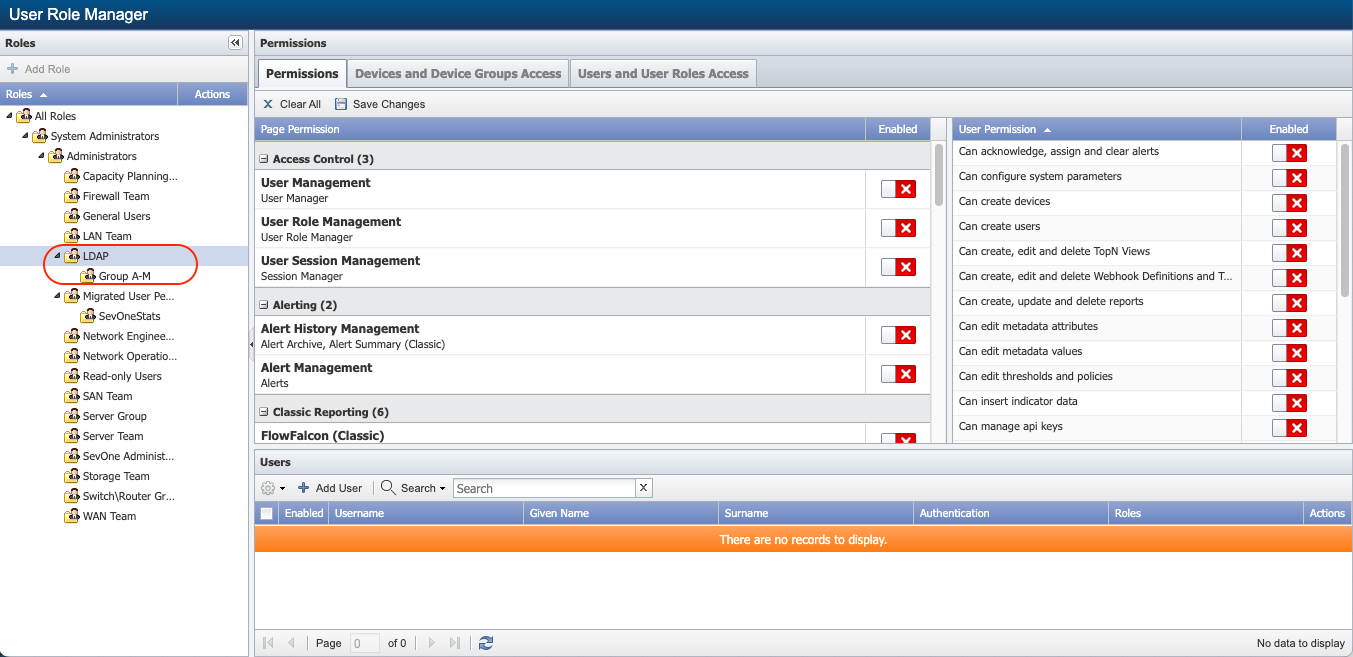
LDAP groups are associated with SevOne User Roles nested in the LDAP folder. The LDAP sync process will automatically perform the following actions:
-
Create or delete User Roles within the LDAP folder hierarchy for any LDAP groups present during the sync.
-
Create new user accounts for any users present in the LDAP groups.
-
Add or remove User Roles to individual user accounts based on their LDAP group assignment.
LDAP roles created by the sync will have no permissions by default and must be maintained manually. If LDAP group assignment is changed for a user, the next LDAP sync will modify the user's roles in the NMS accordingly.
User roles not nested within the LDAP roles folder can be assigned to LDAP users but require manual management by an administrator.
Add Group
-
If the group you are looking for does not appear, click Add Group to display the Add Group pop-up.
 Example
Example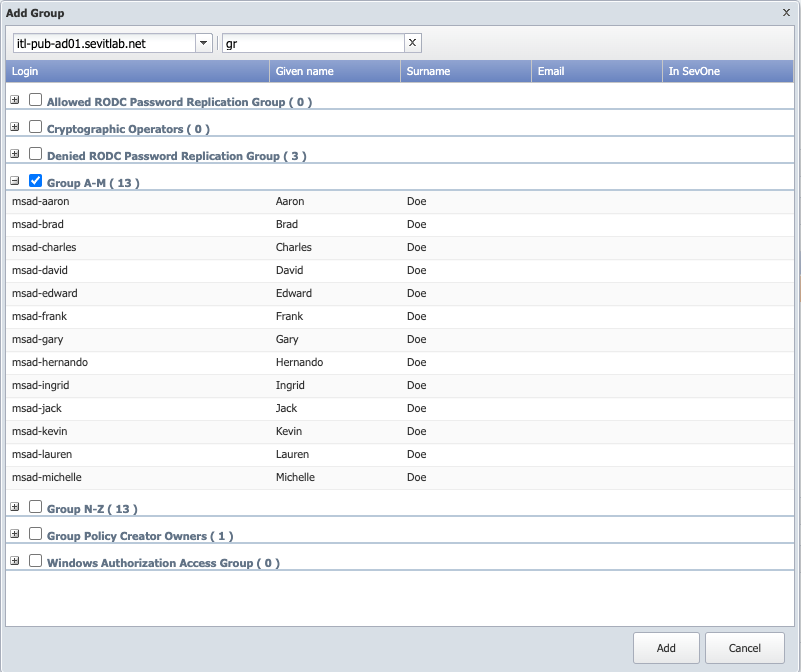
-
Click the LDAP Server drop-down and select a server. For example, LDAP server, itl-pub-ad01.sevitlab.net.
-
In the Search field, enter at least one letter to filter the search results and press Enter.
-
In the list of groups, click the + next to the group name to display the group members.
-
Select the check box for each group to add. For example, Group A-M.
-
Click Add to add the groups you select.
-
-
Click on Delete Selected to remove the group that is currently displayed in the Group: input box. Use the down arrow to select any group you wish to delete. All users that are only assigned to this group will be deleted. Users that have other group memberships will be retained.
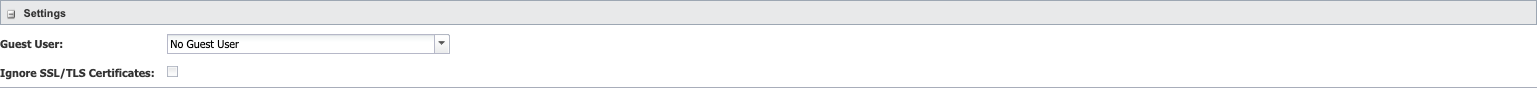
Settings
In the Settings section, click the Guest User drop-down and select the guest user to provide permissions for anyone who logs on with a valid LDAP ID but no SevOne NMS account.
-
Select the Ignore SSL/TLS Certificates check box to skip verification of the server (not recommended). If you change this setting you must contact SevOne Support for it to properly take effect.
Click Save LDAP Settings.
RADIUS
The RADIUS tab enables you to configure SevOne NMS to communicate with the RADIUS protocol authentication server.
RADIUS Servers
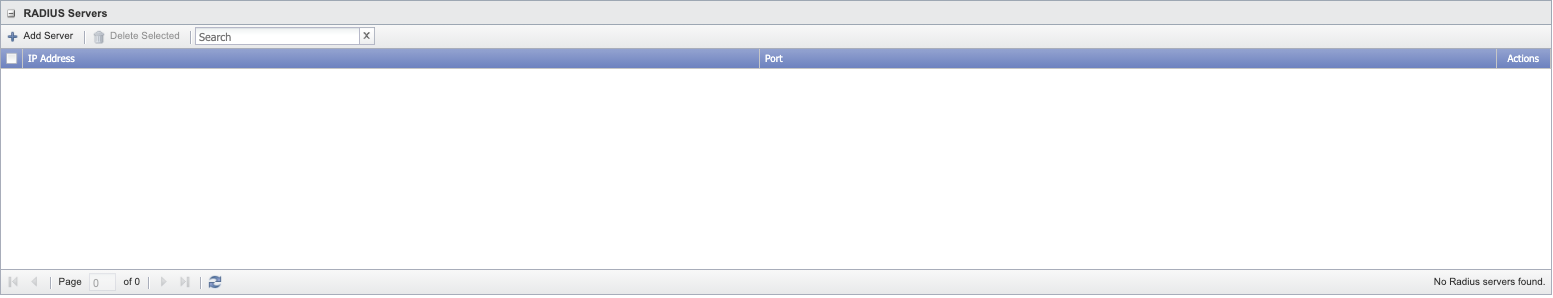
-
Click Add Server above the server list or click
 to display the Add/Edit RADIUS Server pop-up.
to display the Add/Edit RADIUS Server pop-up. 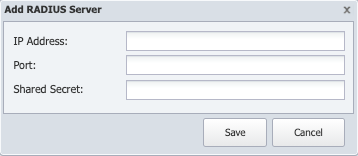
-
In the IP Address field, enter the IP address for the RADIUS server.
-
In the Port field, enter the RADIUS sever port number.
-
In the Shared Secret field, enter the RADIUS server shared secret.
-
Click Save.
-
-
Repeat to add additional servers.
Settings
-
Click the Encryption drop-down and select the type of encryption to use.
-
Click the Guest User drop-down and select the guest user to provide permissions for anyone who logs on with a valid RADIUS ID but no SevOne NMS account.
-
In the RADIUS NAS Identifier field, enter the RADIUS NAS identifier, if required (default - localhost if left blank).
-
In the RADIUS Calling Station ID field, enter the RADIUS calling station identifier, if required (default - 127.0.0.1 if left blank).
-
Click Save RADIUS Settings.
TACACS
The TACACS subtab enables you to configure SevOne NMS to communicate with the TACACS protocol authentication server. The servers in the list are tested in the sequence in which they appear in the list. If the first server is running and the user does not have the proper credentials, then the user cannot log on. If that server is not running then the second server in the list attempts to log the user on.
TACACS Servers
-
Click Add Server above the server list or click
 to display the Add/Edit TACACS Server pop-up.
to display the Add/Edit TACACS Server pop-up. 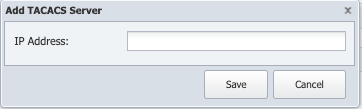
-
In the IP Address field, enter the IP address of the TACACS authentication server.
-
Click Save.
-
-
Repeat to add additional servers.
Settings
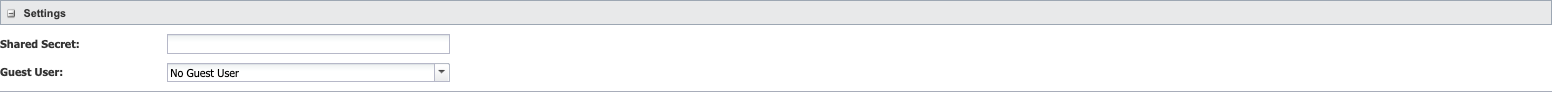
-
In the Shared Secret field, enter the shared secret for the server.
-
Click the Guest User drop-down and select the user to provide permissions for anyone who logs on with a valid TACACS ID but no SevOne NMS account.
-
Click Save TACACS Settings.
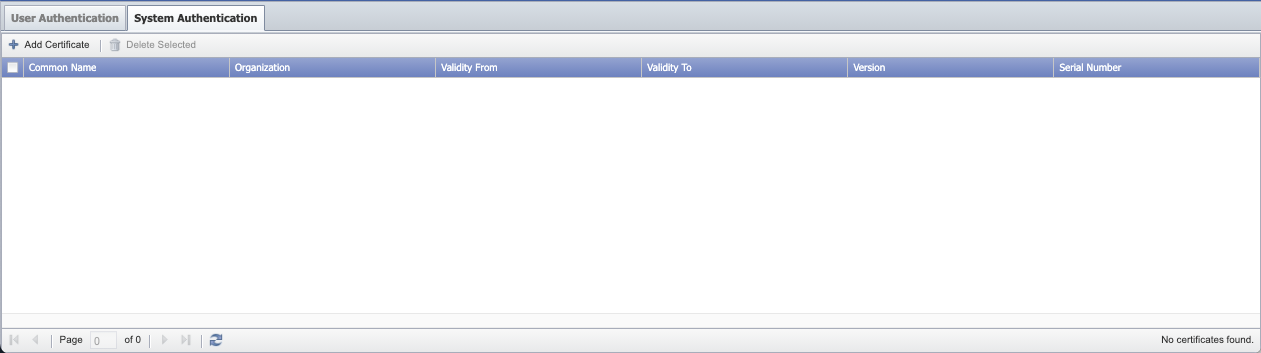
System Authentication
The System Authentication tab enables you to upload security certificates. SevOne NMS uses authentication certificates for LDAP. You also need to upload a certificate if you want to use the HTTP plugin and/or the Web Status plugin with a log on via https. You must upload the CA Root Certificates to enable SevOne NMS to communicate with an LDAP server that has certificates that are signed by an unknown CA. The certificates must be base64-encoded PEM files. It can take up to fifteen minutes for a certificate to synchronize across your SevOne cluster.
-
Click Add Certificate to display the Upload SSL/TLS Root Certificate pop-up.
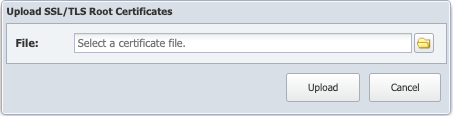
-
Click
 to locate and select the certificate.
to locate and select the certificate. -
Click Upload to upload the certificate.
The System Authentication tab provides the following information for certificates that have been uploaded.
-
Common Name - The hostname that the certificate is associated with.
-
Organization - The organization that the certificate is associated with.
-
ValidityFrom - The date and time from which the certificate is valid.
-
ValidityTo - The date and time at which the certificate stops being valid.
-
Version - The certificate version number.
-
SerialNumber - The certificate's serial number.
Troubleshooting
Check the basics.
It is a good idea to start with the basics. If you have added a server and the connection test has failed, double-check that all the basic settings are correct. Select the server in question and click  to display the Edit LDAP Server pop-up. Check line-by-line to confirm that the information in the fields is accurate. If you used a bind password, try reentering it to see if that fixes the problem.
to display the Edit LDAP Server pop-up. Check line-by-line to confirm that the information in the fields is accurate. If you used a bind password, try reentering it to see if that fixes the problem.
You uploaded a certificate, and the server connection test fails when using StartTLS or SSL.
There are a few possibilities here:
-
The newly uploaded certificate may not have taken effect yet. Just give it a few minutes and try again. If that does not work, proceed to the next step.
-
Something went wrong during the upload. Try uploading your certificate again and wait about five minutes for it to take effect. If that does not work, proceed to step 3.
-
There is a problem with your certificate. If there is a problem with the certificate itself, you may need to get another copy of the certificate file. Upload the new certificate file and wait about five minutes for it to take effect. If you are still having problems after that, the original certificate file may be corrupted. If it is, you will need to get a good certificate file and upload that. Once again, give it about five minutes to take effect.
Terms
|
Authentication |
The process of verifying that someone is who they claim to be. |
|
Authorization |
The process of allowing someone access or information. |
|
Certificate |
A file used to verify that its owner (for example, a server) is who it says it is. |
|
Certificate Authority (CA) |
A trusted third party that issues digital certificates, which certify that the certificate owners are who they say they are. |
|
Encryption |
The process of converting data into a format that can only be read by authorized users. |